“Regrettably the latter seems like the less likely clarification, presented they communicated on different lists regarding the ‘fixes’” presented in the latest updates. These updates and fixes can be found listed here, right here, below, and right here.
Dependable: TCP guarantees that information will likely be delivered as a way and devoid of errors. This helps make TCP more ideal for apps that have to have responsible information transmission.
interaction amongst them. This is especially beneficial in eventualities exactly where the products can be found in remote
Community-crucial authentication is a far more secure choice to password-primarily based authentication. It utilizes a set of cryptographic keys, a general public essential and a private critical. The public essential is saved within the server, and the non-public crucial is saved key via the consumer.
You may e mail the positioning proprietor to let them know you were being blocked. Please consist of what you were accomplishing when this website page arrived up plus the Cloudflare Ray ID identified at The underside of this webpage.
It is possible to connect from A to C applying B to be a gateway/proxy. B and C must each be operating a sound SSH3 server. This performs by establishing UDP port forwarding on B to ahead QUIC packets from the to C.
to its SSH UDP server by means of DNS queries. The server then processes the ask for, encrypts the data, and sends it again
We will increase the safety of information on your own computer when accessing the Internet, the SSH account as an intermediary your internet connection, SSH will give encryption on all information go through, the new mail it to a different server.
OpenSSH: OpenSSH is an open-supply implementation of your SSH protocol suite, recognized for its robustness, safety features, and intensive System support. While it is more source-intensive as compared to Dropbear, OpenSSH's flexibility can make it suitable for an array of programs.
-*Authorization denied Be certain that the person trying to join has the required permissions to obtain the SSH server.
Disable Root Login: Avoid direct login as the root user, as this grants too much privileges. Rather, create a non-root user account and grant it sudo privileges for administrative responsibilities.
You will discover many various ways to use SSH tunneling, dependant upon your needs. One example is, you may use an SSH tunnel to securely entry a distant community, bypassing a firewall or other stability measures. Alternatively, you could use an SSH tunnel to securely access a neighborhood network source from the remote site, for instance a file server or printer.
karena menggunakan Protokol DNS Tunnel maka kecepatan maksimal World wide web hanya mencapai 300KB/s dan akan menurun seiring banyaknya details yang sudah dipakai. tunnel slowdns sangat cocok untuk kebutuhan internet ringan seperti browing chating dan sosial media
Once After i stayed in the dorm I discovered that many non-whitelisted ports and IP ranges have been throttled.
 Daniel Stern Then & Now!
Daniel Stern Then & Now! Michael J. Fox Then & Now!
Michael J. Fox Then & Now! Michael Jordan Then & Now!
Michael Jordan Then & Now!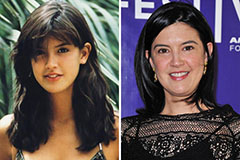 Phoebe Cates Then & Now!
Phoebe Cates Then & Now! Peter Billingsley Then & Now!
Peter Billingsley Then & Now!